What is Ransomware?
Table of Contents: Definition – Social Engineering – Types – Tips and precautions – Pro & cons paying a ransom – Questions – Notes
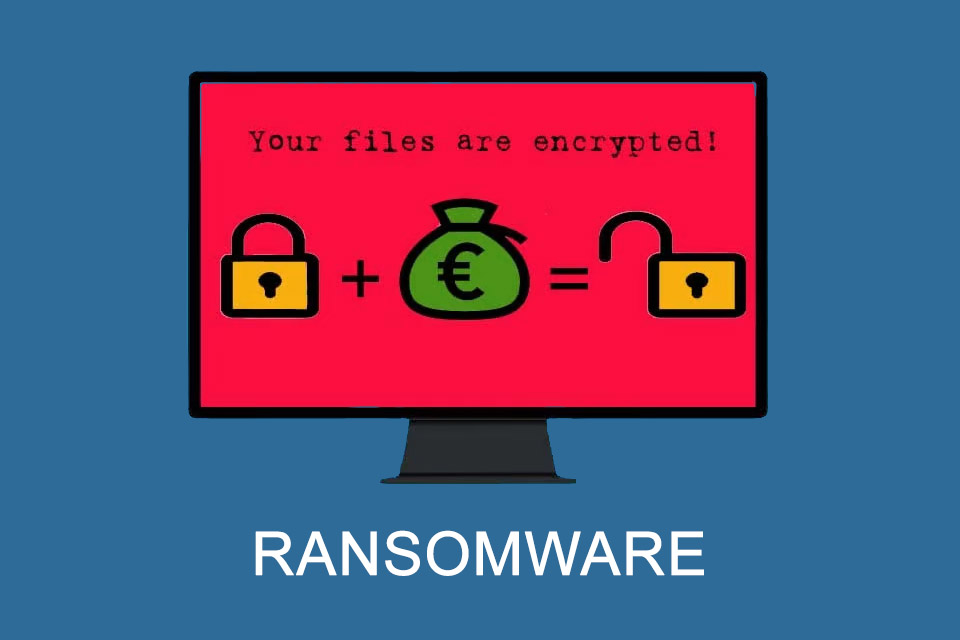
Ransomware – when files are held hostage
Ransomware is malware that encrypts access to networks, computers or computer files using screenlockers or file encryptors. Victims of the offence can – at least in theory – remove the encryption by paying a ransom. In simple terms, ransomware kidnaps computers or computer files and demands a ransom in return for the release, i.e. the ability to use the data again.
Ransomware is a portmanteau of ransom and software. In contrast to “conventional” malware, which tries to harm a computer, a user or a network of computers and their users, the intention of ransomware is to extort ransom money.
Alternative terms for ransomware are blackmail software, data hijackers, encryption trojans or crytotrojans.
What types of ransomware exist?
Ransomware can be categorised into two types:
1. screenlocker or locker ransomware
This type of ransomware locks users out of their systems. As a rule, users only see a lock screen or a screen with a ransom demand. The mouse and keyboard are partially enabled to allow payment to the attacker. Lockers do not normally destroy data, but merely prevent users from accessing it. A timer with a deadline is often displayed to urge the victim to pay.
2. file-encrypter or crypto-ransomware
This is the most common type of ransomware. It encrypts the data, information or files on the victim’s device. The victim can usually see the data and even use the system, but cannot access the data due to the encryption. The crypto-ransomware also asks the victim to pay. If the user misses the deadline, all encrypted data is permanently deleted.
Further (sub)variants can be found in the literature:
Leakware attacks – also known as doxware or doxing – threaten companies, authorities and even private individuals with publishing confidential data in public domains.
RAAS, short for “ransomware as a service”, is a business model in which cybercriminals sell or rent ransomware to other potential attackers. Similar to other Software-as-a-Service (SaaS) models, customers can pay to gain access to ransomware without having extensive technical knowledge.
RAAS providers often provide a user-friendly interface or dashboard that allows customers to personalise and customise the ransomware. For example, they can specify which file types should be encrypted, set the ransom and even receive support. Some RAAS offerings also include affiliate programmes where customers receive a share of the ransoms paid that are generated by their use of the ransomware.
RAAS has greatly facilitated the spread of ransomware in recent years, as it allows potential attackers to carry out ransomware attacks without much effort. It has also led to a wider variety of actors being involved in such attacks, as less technically savvy individuals or groups can easily gain access to ransomware.
Tips and precautions against ransomware
There are a number of tips and precautionary measures to protect yourself as an organisation or user against the threat of ransomware. On the one hand, it is important to minimise the attack surface and, on the other, to optimise personal actions.
- Train employees and make them aware of the extreme dangers. Cyber criminals use psychological tools to motivate people to take action. The employee quickly clicks on the link in the email from the boss without first taking a close look at the sender information in the email, for example. If the email only appears to come from the boss, every link click in the email can have far-reaching consequences. Of course, employees should never click on links or attachments in emails from unknown senders.
- Update operating systems and software with the latest patches, but only from sources you know and trust. Outdated applications and operating systems are the target of most attacks.
- 123456 is many things, but it is not a secure password. Use secure passwords and multi-factor authentication.
- Back up your data regularly. Some sources recommend creating 3 copies, using 2 different types of storage for them and storing 1 copy offline. Ideally, you should also back up system images, application software and configurations. It also makes sense to use unalterable backups that can no longer be manipulated or deleted. And also test the recovery process in terms of speed, completeness and costs.
- Restrict the authorisations for installing and running software applications on your computer.
- Set up non-privileged mail accounts for administrators for everyday purposes, which allow them to read emails, surf the Internet, etc., but at the same time limit the effects of clicking on a phishing email.
- Use whitelists of applications that can be run on the network.
- Use spam filters to ideally prevent phishing emails from reaching end users. Authenticate incoming emails to prevent email spoofing.
- Configure firewalls to block access to known malicious IP addresses. And segment your network so that, in the worst case, viruses can only spread in one segment.
- Monitor the system and monitor the logs. Be informed when a new administrator account is created.
It is generally assumed that around 75% of all malware attacks are carried out via phishing. It is therefore particularly important to make employees aware of the dangers and train them in the correct procedures.
Pros & cons: paying a ransom
And what should you do if you have fallen victim to ransomware? Paying a ransom for ransomware is often the subject of controversy. Some advocates argue that paying a ransom is the quickest and easiest way to restore access to encrypted data and resume business operations as quickly as possible. However, there are also numerous risks and ethical concerns associated with this practice.
Here are some arguments in favour of pro ransomware:
- One of the main arguments in favour of paying a ransom is to be able to use the locked files again. Especially if the data and files have a high value for business operations, there is practically no alternative to paying.
- One argument in favour of paying a ransom is that it enables companies to resume operations quickly without having to go without access to the data for long periods of time. Especially for companies whose business activities are heavily dependent on the availability of their data, paying a ransom can be the quickest solution to avoid business interruption.
- Publicly publicised attacks can shake the confidence of customers and investors in a company. By paying the ransom and restoring operations, companies can limit the damage to their image and regain the trust of their stakeholders.
- In some cases, the financial damage of an attack can be limited by paying the ransom. The cost of restoring data and systems and the potential loss of revenue due to business interruption could be higher than the ransom demanded.
And here are some arguments against ransomware:
- There is no guarantee that the attacker will actually release the data after the ransom is paid. Even if the ransom is paid, the encrypted data may remain corrupted or unreadable.
- There is no mechanism to prevent the attacker from repeating the ransom demand. One-off payments could make organisations a repeat target for attacks, as the attackers could see that the victim is willing to pay. Perpetrators do not have to abide by any code of honour or fear unkind judgement from victims.
- The payment of ransom funds criminal activity and helps to ensure that ransomware remains a lucrative source of income for cybercriminals. This can encourage other potential attackers to carry out similar attacks.
It is not easy to make a decision and affected companies or individuals will not find any definitive guidance here. How high is the ransom demand? Is it even legally permissible to pay a ransom? Is there a threat of fines? Situations are often individual, so they also require individual decisions. Contacts such as the Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik – BSI), the Federal Criminal Police Office (Bundeskriminalamt – BKA) or the US Cybersecurity and Infrastructure Security Agency (CISA) recommend on their websites not to comply with ransom demands, but in case of doubt, those affected should seek professional expertise in order to make an individually informed decision.
Questions from the field
Here you will find some questions and answers from the field:
How long has ransomware been around?
The AIDS Trojan disc is considered to be the first ransomware. In 1989, the evolutionary biologist and Harvard graduate Joseph L. Popp sent out 20,000 infected discs with the inscription “AIDS Information Introductory Diskette”. In this way, the ransomware even reached the computers of participants at the World AIDS Conference of the World Health Organisation.
The AIDS Trojan disc replaced a system configuration file and began to encrypt the hard drive after ninety reboots. In order to regain access to their data, the victims were asked to send 189 US dollars by post to the company PC Cyborg in Panama. For this reason, the first ransomware was also known as the PC Cyborg Trojan.
In 2005, the first encryption Trojan TROJ_PGPCODER.A was distributed via the Internet. At the time, the blackmailers demanded several hundred dollars for decryption.
What is the difference between ransomware and malware?
Malware aims to penetrate computer systems and cause damage. Ransomware is a special form of malware that aims to encrypt files on an infected system and then extort a ransom to release the files again.
In addition to ransomware, there are also other types of malware such as spyware, adware, Trojans or viruses. These have different goals and effects, such as collecting personal data and information, stealing personal files, displaying unwanted adverts or damaging files or systems.
In short: ransomware is a type of malware; malware is not always ransomware.
What does software against ransomware do?
Software can help against ransomware in various ways:
To recognise already known ransomware families, there is a simple method: the use of signatures. These signatures identify specific command sequences in the code of a file that are characteristic of a certain group of malware programmes. They can also recognise generic code sequences that indicate typical malicious actions such as compression, encryption and backdoor activity.
Another strategy is to monitor network traffic to prevent the activation of ransomware. This involves blocking access to the control servers. Behaviour-based detection monitors running applications for suspicious activity and aims to recognise the first actions of malware. This also includes the exploitation of security vulnerabilities via manipulated websites.
Characteristic processes can be recognised during the installation of ransomware, such as the creation of configuration files and registry entries. To combat the persistence of ransomware after a system restart, typical autostart mechanisms are recognised and interrupted.
The spread of ransomware via websites is combated by collecting and blocking malicious URLs. The malicious code in the browser data is also checked. In addition, virus scanners check email content at an early stage to prevent malicious emails from being delivered in the first place.
Where can you find expert support in the event of a ransomware attack?
The BSI provides a catalogue of measures (https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/Cyber-Sicherheit/Themen/Ransomware_Massnahmenkatalog.html) for free download (in German).
In Switzerland, the Reporting and Analysis Centre for Information Assurance MELANI offers help. Among other things, MELANI publishes semi-annual reports on the development of ransomware.
The European Cybercrime Centre – EC3 also offers a lot of useful information.
“Overlooked. Forgotten. Neglected.” – These three human things are exploited by attackers.
Notes:
If you like the article or would like to discuss it, please feel free to share it in your network. And if you have any comments, please do not hesitate to send us a message.
Here you can find a video on how to combat ransomware.
Here you will find additional information from our Smartpedia section:

Social engineering: How does ransomware get onto computers?
The answer to this question is almost always: social engineering.
There is a risk factor in every organisation that is difficult to control, even with the best technical security measures: people.
Social engineering is about influencing people. The social engineer, aka the perpetrator, attempts to gain the victim’s trust in person, by telephone, post or digitally, e.g. via email, messenger or chat, in order to obtain confidential information or install malware.
Social engineering – also known as social manipulation – does not require any special programming skills. Technical barriers are overcome through the use of psychological tricks. The following methods are relatively common:
Phishing is a common method in which emails are sent to a large number of recipients in order to persuade them to take a certain action. These actions can include clicking on a link, filling in a form or confirming their identity. Phishing methods are varied and range from automated mass emails to targeted attacks. Nevertheless, the success rate is comparatively low, as the emails are often recognised as fraudulent or moved directly to the spam folder. This is because they are not customised to the recipient.
Spear phishing is a method of targeted social engineering that requires significantly more resources than conventional mass fraud. It involves targeting specific groups of employees in a specific industry. Unlike conventional phishing, where a wide net is cast, the perpetrators select their victims specifically.
Professional social engineers go one step further and take the risk of targeting just a few selected employees or even individuals within a company. They gain the trust of their fraud victims over a longer period of time by building up a relationship and studying their behaviour. They also falsify complex references to bolster their credibility.
Preparations for such sophisticated fraud schemes can take weeks or even months. However, the high level of effort is worth it, as the success rate for these sophisticated attacks is very high. Otherwise, the intensive use of resources would not be justified.
Vishing – the term is made up of the words “voice” and “phishing” – is a fraud method in which fraudsters attempt to obtain personal information from their victims by telephone. The perpetrators often use techniques such as caller ID spoofing, where they manipulate the caller ID to make it look like a legitimate number. Alternatively, they pretend to be representatives of well-known institutions such as banks, government agencies or technology companies. They use the call either to obtain sensitive information directly from victims or to trick them into accessing fraudulent websites or links where they are then asked to disclose their details.
In baiting, victims are tricked with a lure (USB stick, CD, SD card from a seemingly trustworthy source or promotional gift) into using a data carrier that contains malware.
Pharming is a type of cyber attack in which a victim’s DNS (Domain Name System) servers are manipulated in order to redirect them to fake websites. The term “pharming” is made up of the words “phishing” and “farm”. The attackers either manipulate the victim’s DNS entries directly or infect their computer with malware that changes the DNS settings. As a result, victims are redirected unnoticed to fake websites when they enter legitimate URLs.
Scareware aims to scare users with alarming messages and trick them into downloading malware. The attackers often use deceptively genuine and legitimate prompts that urge the user to act quickly without leaving much time to think or analyse. These prompts can take the form of pop-up windows, threatening messages or fake buttons, displaying alarming messages such as: “Your PC is very slow. Speed it up now” or “Protect your IP from attackers now!” Users who fall for these tricks allow the ransomware to infiltrate their systems and lock them or encrypt their data.
In short, social engineering can take many forms. Social engineers often combine different methods, which also makes it difficult for people in organisations to recognise such scams in time.