What is a Backend?
Table of Contents: Definition – Distinction between Frontend and Backend – Technologies and Programming – Challenges – Tips – Notes
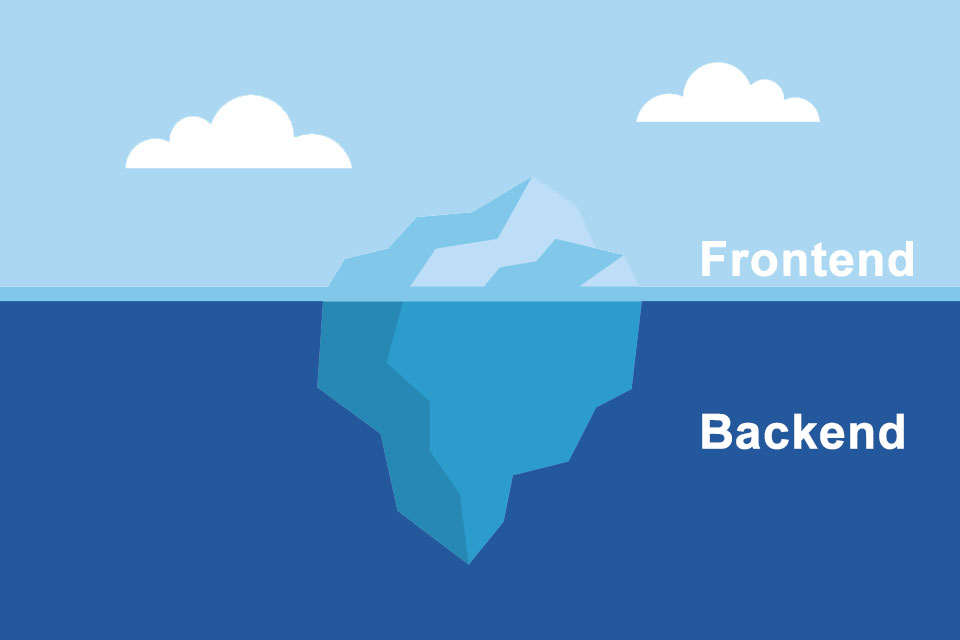
Backend – the foundation of an application
In software technology, the backend refers to the server-side logic and data storage of a software application. It is the part of the software that is not directly visible to the user, but is responsible for all functions that run in the “background” or “substructure”.
The backend
- contains the business logic with the core functions of an application.
- processes data entered by users or received via interfaces.
- performs calculations and operations on this data and makes the results available to the frontend.
- interacts with databases to retrieve, consistently store and update data.
- provides application programming interfaces (API) through which other applications and services can access its functions and data.
In short, the backend is the foundation of an application.
Application examples for the distinction between frontend and backend
If the backend refers to the invisible part of a software application, then the frontend includes the visible part. In the course of information technology, one also likes to speak of a layer division or layer architecture1. Below you will find some application examples for differentiation:
- In a client-server application, the programme running on the client is called the frontend and the one running on the server is called the backend.2
- In a database application, the user interface – with its forms and reports – is assigned to the frontend, tables, views or the stored procedures to the backend.
- In web-based applications, the user interface for users is declared as the frontend, the system access for defined specialist groups as the backend.
- In content management systems, the visible part – the website – belongs to the frontend, the administrator area for managing the website and for creating and maintaining content to the backend.
These four examples of use show that both terms are used in a related way, but they are not really 100 % congruent. Often, a user uses a frontend without thinking about the backend that provides the correspondingly required services. Ideally, the user does not notice whether the application interacts with other systems and databases in the background, and in most cases it should not matter to him.3
Technologies and programming languages for backend development
A variety of technologies and programming languages are available for backend development, depending on the specific requirements and preferences of the developers or the clients. Here are some commonly used technologies and programming languages:
- Java is a widely used and robust programming language that is commonly used in enterprise development. It is well suited for large and complex applications.
- Python is known for its simplicity and readability and is used in various frameworks such as Django and Flask. It is also widely used in data science and AI applications.
- Node.js is a server-side JavaScript runtime environment used for real-time web applications and APIs. It is particularly popular for its scalability and performance.
- Ruby is often used with the Ruby on Rails framework and is known for its elegance and productivity in web development.
C# is often used in combination with the ASP.NET framework for web application and enterprise software development, especially in the Microsoft ecosystem. - PHP has long been one of the most widely used languages for web backends. It is used in numerous content management systems (CMS) such as WordPress and Drupal.
- Rust is known for its security and performance and is mainly used in the development of safety-critical applications.
- SQL databases such as MySQL, PostgreSQL and NoSQL databases such as MongoDB and Redis are commonly used to store data.
- Cloud platforms such as Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP) offer services and tools for developing scalable and maintainable environment.
The list of technologies and programming languages can easily be extended.4 The choice in a specific case depends on the specific requirements of the project, the experience of the developers and the goals of the application. Often, developers also use a combination of different technologies and services to achieve the best results.
Challenges in backend development
Backend development can present several challenges. Here are some of these challenges and approaches to overcoming them:
- Over time, user numbers and data volumes often increase. The keyword is scaling. Using scalable architectures such as microservices and cloud computing platforms often proves to be very useful.
- Backends need to be protected from various security threats, including attacks such as SQL injection, cross-site scripting (XSS) and denial-of-service (DoS). To minimise security risks, best security practices such as data validation, authorisation checking and encryption should be implemented.
- Efficient database management and optimisation can be challenging. This requires the use of appropriate database engines, indexing strategies and database queries to optimise performance.
- Identifying and fixing errors can be time-consuming. To facilitate this, comprehensive logging and monitoring should be implemented to recognise and diagnose problems early.
- Backends often need to communicate with various external services and APIs. To minimise interoperability issues, clear API specifications and robust error handling should be implemented.
- Developing comprehensive and easy-to-understand documentation for the backend is important to facilitate other developers and integrators.
- The backend should be structured to facilitate future extensions and updates without compromising the stability of existing functionality. Using modular code and following best development practices can help.
- Ensuring data quality and cleaning up inaccurate or outdated data in the database can be time-consuming but crucial for smooth operations.
- Legal requirements and data protection regulations must be observed when developing backends, especially if personal data is processed. This often requires the implementation of data security mechanisms and compliance checks.
- Comprehensive testing, e.g. in the form of integration tests and load tests, is important to ensure that the application functions reliably and without errors.
Overcoming these challenges requires a deep understanding of back-end development, careful planning and the selection of appropriate technologies and tools. It is also important that development teams work closely together and adhere to best practices in software development to create robust and secure backends.
Tips for backend development in terms of security and scalability
Security and scalability are two key success factors when developing backends. Below are some tips:
- Implement robust authentication mechanisms to ensure that only authorised users and systems can access the backend. Use authorisation to ensure that users can only access those resources for which they are authorised.
- Validate and filter all user input to protect against attacks such as SQL injection and cross-site scripting (XSS). Use secure escape functions to safely insert user input into application data.
- Be careful to avoid vulnerabilities listed in the OWASP Top Ten list5 such as insecure direct memory access, insecure deserialisation and API security issues.
- Encrypt sensitive data in the database and during transmission between the frontend and the backend. Use strong encryption algorithms and secure key management.
- Implement secure session management and token management to protect user sessions and ensure session information is not compromised.
- Implement comprehensive logging and monitoring to recognise anomalies and security incidents. A good logging system is critical for error handling and security monitoring.
- Consider using a microservices architecture, if necessary, to split the application into smaller, independent services that can scale more easily.
- Implement load balancing to distribute traffic evenly across multiple servers or containers for better scalability and availability.
- Use caching mechanisms to cache frequently accessed data and improve response times.
- Optimise database access by using efficient queries and indexing. Use scalable database systems.
- Automate provisioning processes and use orchestration tools to enable scaling of services on demand.
- Implement comprehensive monitoring to track performance. Scale resources in a timely manner to meet demands.
Use these tips to ensure that backends are secure, stable and scalable. Ideally, they should be followed throughout the development lifecycle to recognise and address potential problems early.
Impulse to discuss
Conway’s Law states that the structure of a system to be developed is predetermined by the communication structure of the implementing organisation. If, for example, there is a front-end and a back-end development team, this can be problematic. What are the pros and cons of using functional teams to take care of both layers when developing a feature?
If you like the article or would like to discuss it, please feel free to share it in your network. And if you have any comments, please do not hesitate to send us a message.
[1] Layering or layer architecture is a structuring principle of software systems.
[2] There are situations in which the frontend must also have its own “logic”. Here it can make sense to apply the BFF pattern (backend-for-frontend pattern) in the development.
[3] A good example might be ChatGPT. Users use the service without thinking about the internal architecture or the interaction of different services in the ChatGPT network.
[4] JavaScript is widely used for front-end development, especially for the design and behavior of web pages and web applications in the web browser. However, the popularity of Node.js has encouraged the use of JavaScript in the backend. Here you can find relevant JavaScript basics.
[5] The OWASP Top 10 is a standard document for raising developer awareness of web application security.
And here you can find supplementary information from our t2informatik Blog: