The interplay between cyber security and business analysis
The rapid development of computer technology and digitalisation has profoundly changed our society over the last five decades. The paperless office1, for which a patent application was filed back in 1978, was the first indicator that heralded the transformation of analogue information into digital representations and thus the transfer of processes to the computer world. Today, digitalisation is a driver of innovation and efficiency, but it also harbours a central problem: digitised data cannot simply be locked away in a filing cabinet. For example, without suitable measures, it can be duplicated easily and as often as desired and read or shared by unauthorised persons. We need protection for our data and digital worlds, we need cyber security.
In this article, I would like to shed light on the interplay between cyber security and business analysis, identify sources for cyber security requirements and highlight some best practices for data security. Let’s go.
What is cyber security?
Digitalisation and the penetration of technology into our economy and our lives have led to cyber security becoming one of the most important topics for companies, authorities and private individuals.
Wikipedia defines the term as follows: “Computer security: the security of a computer system against failure (referred to as unplanned or planned downtime) and manipulation (data security) as well as unauthorised access“.2
Cyber security therefore encompasses not only the protection of data, but also of systems and ensures their availability. The acronym CIA has also become established for this. CIA does not stand for the Central Intelligence Agency, but for Confidentiality, Integrity and Availability of Information.
Confidentiality ensures that only authorised persons can access data or an information system. Confidentiality means that data is not made accessible or disclosed to unauthorised persons, facilities or processes. The encryption of data is a key element in ensuring confidentiality.
The property of integrity ensures that the data or information system is trustworthy, is only processed by authorised persons and remains in its original state when at rest. Integrity means that the correctness and completeness of the data is guaranteed throughout its entire life cycle. Data encryption and hashing algorithms are used to ensure integrity.
The availability of information means that data and information systems must be available when required, i.e. the systems for storage, processing and also the necessary communication channels (Internet) must function flawlessly.
Motivation for more cyber security
As digitalisation now permeates all areas of a company, cyber security has evolved from a specialist area of technology to an integral part of companies. This is also reflected in the fact that positions such as the Chief Information Security Officer (CISO) have been created at C-level.
The motivation of organisations is easy to explain: a lack of cyber security has consequences! Be it directly through penalties that can be imposed if data is lost or misused. Or indirectly through loss of reputation if the company’s website has been hacked or the network has been taken over by a crypto trojan.
Here are some current examples:
- The average cost of a data breach to a company is $4.45 million, according to IBM.3
- The cost of an attack by third parties (e.g. partners or suppliers) is $4.63 million, $370,000 higher than the average of $4.26 million, which emphasises the importance for companies to closely examine the security of the companies they do business with.4
- Forty per cent of cybersecurity attacks are estimated to originate in the extended supply chain.5 A prominent example is perhaps the massively exploited vulnerability in Confluence, which forced companies to switch to paper or alternative forms of collaboration for days at a time.6
- The costs of a crypto trojan attack are difficult to calculate and can range from a business interruption of a few hours to several weeks of downtime. If a ransom is paid as a result of ransomware, payments in the millions are possible.7
Shift left into the business analysis
Costs are another reason to position cyber security as early as possible. For a long time, security was only ever a part of IT, but developments in recent years have meant that cyber security has increasingly become a general task for management and therefore also for business analysis.
The often purely technical, so-called non-functional requirements have become business or stakeholder requirements and have therefore increasingly become the focus of business analysts.
Business analysis is “the practice of enabling change in an organisation by defining needs and recommending solutions that offer added value to stakeholders. Business analysis enables an organisation to formulate the demand and reasons for change and to design and describe solutions that can add value”.8
Business analysis is therefore not limited to people with a specific certification or training, but business analysis is an activity.
Other common job titles for people include Business Architect, Data Analyst, Business Analyst, Process Designer, Product Manager, Product Owner, Requirements Engineer, Tester or even UX Designer. Nevertheless, the role of business analyst has become established in the English-speaking world and describes someone who carries out business analyses as their main job.
In addition to the term business analyst, there is also the cyber security analyst, who in my opinion is no different from a business analyst. Both do business analysis, the only difference is the depth of cyber security knowledge and the focus of their daily work. While the business analyst mainly deals with business processes and business requirements and cyber security is only part of their work, the cyber security analyst has very in-depth technical knowledge. In addition to
- continuous education and training in security technologies
- also he manages applications in the company,
- monitors activities in the network,
- manages assets and
- defines and implements security measures.
What is a cyber security analysis?
A business analyst carries out a cyber security analysis as part of their work. The cyber security analysis forms the basis for planning and preparing a secure environment. Business analysis is about understanding the requirements and their value, and cyber security is about building security into everything we work on, not just tinkering with it after the fact.
The role of the business analyst in cyber security is first and foremost to ensure that the organisation is implementing and applying these policies, tools and procedures properly. However, this also includes identifying all relevant stakeholders (stakeholder management) and gathering cyber security requirements (requirements management).
Sources for cyber security requirements
The aim of the business analysis should be to define all cyber security requirements. Missing requirements usually lead to delays in the project and, in the worst case, to project cancellation. Special care is therefore required here.
A number of standards have emerged in the area of requirements that can serve as a starting point for the analysis and are most likely already being used in some companies. Here is an exemplary selection:
- ISO/IEC 270009: standard for information security management from the International Organisation for Standardisation (ISO) and the International Electrotechnical Commission (IEC); helps organisations protect their information through effective technologies, audit and testing procedures, organisational processes and employee awareness programmes.
- COBIT – Control Objectives for Information and related Technology10: The focus is on providing a comprehensive framework for IT governance, including the alignment of IT with business objectives, the management of IT risks and the measurement of IT performance. The COBIT Focus Area: Information Security is certainly the most interesting resource in terms of cyber security.
- ITIL, The IT Infrastructure Library: Contains comprehensive and publicly accessible professional documentation on the planning, provision and support of IT services. ITIL focuses on providing best practices for the management of IT services and thus covers the area of availability.
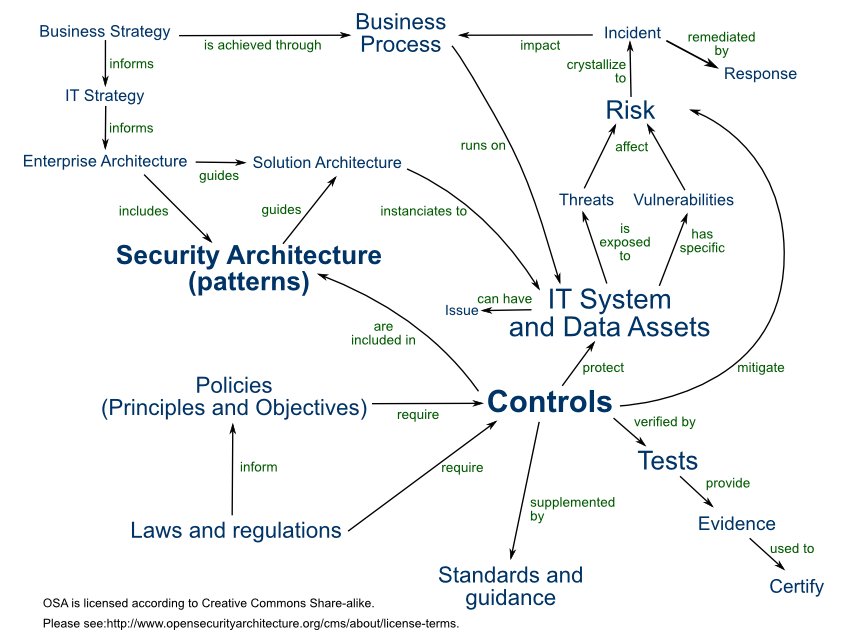
- OSA, Open Security Architecture11: OSA distils the expertise of the security architecture community and provides easy-to-use patterns for your application. It is a free framework developed and owned by the community.
- DPA – Data Protection Act 2018: Sets out the framework for data protection law in the UK; updates and replaces the Data Protection Act 1998 and came into force on 25 May 2018.
- GDPR – General Data Protection Regulation of May 2018: Regulation of EU law on data protection and privacy for all citizens; sets out the main principles, rights and obligations for most processing of personal data.
- PIPEDA – Personal Information Protection and Electronic Documents Act: A Canadian privacy law that regulates how private companies collect, use and disclose personal information in the course of their business.
- Although there is no overarching data protection law in the USA, laws such as the Health Insurance Portability and Accountability Act (HIPAA) may apply to compliance with standards.
- National Institute of Standards & Technology (NIST) Cyber Security Framework: Consists of standards, guidelines and best practices for managing cybersecurity risk and promoting the protection and resilience of critical infrastructure and other sectors important to the economy and national security.
Important: You need an expert to sort all this out – don’t try to do it yourself! Hire a lawyer or contact your legal department to find out which regulations apply to your organisation and work with legal counsel to derive specific requirements from each regulation.
Best practices for data security
“Data is the new gold” is a common refrain, and data is also an important component for a business analyst because
- processes need data to make decisions,
- processes generate data for further processes,
- decisions are often (or at least should be) data-based and
- data is a commodity and therefore also has a value (see monetisation of social media).
Data is no longer just an “appendage” of processes, but is often already part of the core of a company. The main task of a business analyst will therefore be to model and categorise data and take care of its security.
Without reading all the frameworks or getting lost in a legal jungle, simple rules can be applied to increase the security of data. This can be done without consulting a lawyer or legal department.
The following best practices can have a positive effect during design and implementation:
- Data minimisation: limiting the data to be used in a solution by examining the reasons for its collection and confirming that the data collected is the minimum required for the purpose or use case. And this is not only best practice in the EU, but is even law under the GDPR.12
- Pseudonymisation: The assignment of an artificial identifier to replace personal data in order to minimise the amount of personal data processed by an application.
- Anonymisation: The process of separating data about an individual from information that could identify that individual in a broader context. Note that pseudonymisation is not necessarily anonymisation.
- Data retention: The process of determining how long an organisation must retain certain information and deleting that information after the retention period has expired. Delete unused and unneeded data!
- Defence in depth: An approach in which the protected assets have several independent layers of security. This includes network layers (network and subnetworks) as well as general controls such as password protection, encryption and access control for resources including data.
- Privacy by design: The practice of integrating privacy requirements into a technical solution and associated processes during the design phase of a project, rather than as an afterthought.
- Data masking: The practice of replacing real personal data with fictitious data. For test systems with a copy of the production data, masking the imported data is a good practice. Another option is to generate test data with synthetic data that has been artificially created, but the model has been trained with original data. The generated data thus reproduces the properties and structure of the original data.
- Data scrambling or blending: The process of swapping identifying information so that it can no longer be associated with itself. For example, by swapping first names, surnames and dates of birth between data records within a data set until the data no longer represents a real person.
In addition to these often one-off best practices that can be applied during a project phase, ongoing activities should also be carried out. Below are some examples of recurring activities:
- Security benchmarking: How does a company’s security architecture compare to other companies, how does it compare to industry standards and best practices, and where are there gaps and deficiencies that reduce the company’s overall maturity level?
- Policies: Guidelines are high-level management statements that define what is and is not allowed in the organisation. They should be broad enough to cover the entire organisation and be approved by those responsible. They must be regularly reviewed to ensure that they are up to date and adapted as required.
- Internal and external audits: Cyber risks are constantly evolving, quickly and unexpectedly. As cyber risks are wide-ranging and interconnected, they are particularly difficult to manage. These audits often include a review of the correct implementation of company policies.
+ Companies should implement a programme for continuous monitoring and testing of security controls and their implementation.
+ External audits typically review network security using techniques such as penetration testing to ensure that no unauthorised users have access to company resources. - Ongoing risk management: Organisations should conduct periodic and regular management reviews, including review of processes and systems, using self-assessment of controls and driven by the business unit’s risk profile and the manager’s span of control.
Conclusion
Cyber security is a critical topic for all companies and an essential area of knowledge for organisations. It has long ceased to be a purely technical topic and affects all business analysts and many other professionals.
In my opinion, business analysts have a duty to acquire basic knowledge and skills in the area of cyber security. This includes not only knowledge of the relevant laws, but also experience with the aforementioned best practices, as well as active collaboration between companies, business analysts, architects and subject matter experts to create a secure environment in the long term. Let’s go!
Notes:
If you are interested in further information and perspectives in the context of digitalisation, then it is definitely worth taking a look at Gottfried Szing’s blog: https://kjoo.be.
[1] Patent: The Paperless Office
[2] Wikipedia: Informationssicherheit
[3] Cost of a Data Breach Report 2023
[4] Data breach costs for critical infrastructure
[5] Securing the supply chain
[6] Atlassian Confluence vulnerability under widespread attack
[7] Foxconn electronics giant hit by ransomware
[8] BABOK by IIBA
[9] ISO/IEC 27000
[10] COBIT
[11] OSA
[12] GDPR: Principles relating to processing of personal data
If you like the article or want to discuss it, please feel free to share it in your network.
Gottfried Szing has published two more posts in the t2informatik Blog:

Gottfried Szing
Gottfried acts as a “translator” and “departmental understanding” who mediates between the individual groups of people and contributes to the solution. He is a founding and board member of DLT Austria, an association for the sustainable promotion of distributed ledger technologies in Austria. He is also a co-founder of the Meetup groups Domain-Driven Design Vienna and Microservices, Reactive and Distributed Systems Vienna, both of which aim to build better software.
In the t2informatik Blog, we publish articles for people in organisations. For these people, we develop and modernise software. Pragmatic. ✔️ Personal. ✔️ Professional. ✔️ Click here to find out more.