What is a Whitelist?
Smartpedia: A whitelist lists products or organisations that meet defined criteria, are considered trustworthy and are suitable for use or collaboration.
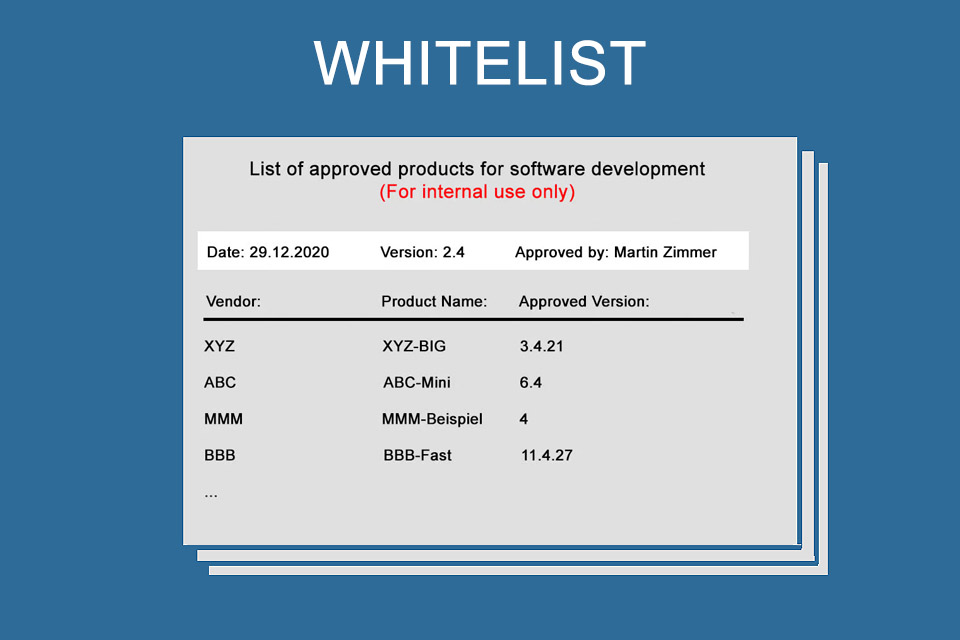
Whitelist – the document of trust
A whitelist is a tool for organisations to list similar elements – e.g. companies, people, products, services – in which the organisation has confidence. For example, a list of partners or recommended companies is a whitelist. Or a list of software tools that have been marked as “suitable for use” after appropriate review by a central enterprise instance.
The basis for such a list is the fulfilment of defined criteria; these are individually specified and checked by organisations.
Whitelisting – the process of creating and maintaining a corresponding list – usually has direct consequences¹: products or services that are not listed may not be used in organisations. And organisations are not allowed to do business with companies or persons that are not on the whitelist. A whitelist therefore determines WHO or WHAT is considered “positive”; therefore, the term positive list is used as an alternative. Another synonym is exception list.²
The opposite of the whitelist: the blacklist
The synonyms positive list and exception list together express the essence of corresponding lists: A positive list suggests, figuratively speaking, positive and therefore good, recommendable entries. An exception list contains the exceptions to the rule, i.e. everything that has not been specifically listed is generally prohibited.
A backlist is the exact opposite of a whitelist: Anything is allowed as long as it is not on the list. So while companies try to get themselves or their products and services on the whitelist of a desired client or partner, they will do everything in their power not to appear on a blacklist.
Examples of whitelists or blacklists
In IT there are many areas of application for whitelists and blacklists. Here you will find some “technical” examples:
- Spam filters offer the possibility of entering IP addresses, e-mail addresses or domain names of senders on a whitelist to protect their e-mails from being rejected or sent to a junk mail folder.
- Firewalls use whitelists or blacklists.
- Content management systems offer possibilities to block or release commentators and manage them in lists accordingly.
- Adblockers have features to allow ads from defined sources.
In addition, companies have individual lists that do not lead directly to a technical “block”, but must be checked by organisational measures – e.g. by taking inventory:
- A list of suppliers with whom one cooperates.
- A list of programs that may be used in an area. Alternatively, this is also called an application whitelist.
- A list of products (smartphones, laptops, etc.) that employees are allowed to use for their work.
There are also numerous examples of whitelists outside IT:
- The Peta Deutschland e.V. lists various positive lists, e.g. for detergents and cleaning agents or food producers without animal testing.
- PHINEO – a non-profit analysis and consulting company for effective social commitment – awards a seal of approval. The aim is to promote non-profit organisations. Phineo explicitly points out that there is no blacklist of companies that have tried in vain to obtain the seal.
- The Central Committee of German Agriculture maintains a positive list for straight feeding stuff.
- And German federal authorities are increasingly conducting bidding competitions in which the winners end up in a pool of possible suppliers (in other words, on a whitelist), who are then asked for concrete offers when individual services are called up in an accelerated procedure.
The criteria for creating a positive list
As the various examples show, positive lists are used in many areas. Depending on the area and content, the criteria that lead to an organisation, products or services being positively listed vary, of course. Companies that want to do business with other companies, for example, may have to
- go through audits,
- provide supporting evidence,
- accept liability or warranty regulations,
- agree to terms of payment,
- guarantee reaction times,
- store source code in bank deposit boxes,
- or provide access to office space.
For application whitelists, for example, it might be necessary, to
- support digital signatures,
- use cryptographic hashes,
- restrict the execution to defined network areas,
- support monitoring of libraries, scripts, macros, browser plug-ins, add-ons, configuration files or registry entries
In practice, there are two procedures for Application Whitelisting:
- Using information from vendors that are considered trustworthy, supplemented by your own findings.
- The technical review of applications and, in the case of “clean” operation, the definition of a baseline.
The combination of both approaches should offer the greatest security.
It is advisable to version a whitelist so that it is clear to all parties involved from which date which version of the list is current and binding.
Advantages and disadvantages of the whitelist
A whitelist offers the following advantages:
- Clarity about permitted products, programs or services or about trustworthy companies, organisations or persons.
- Commitment in the selection and use of products, services or companies.
- Security that the products and services meet defined criteria and are therefore suitable for problem solving.
- Acceleration of selection processes, as the listed products, services or companies represent a pre-selection.
On the other hand, there are also some disadvantages:
- The definition and verification of the criteria is time-consuming.
- Maintenance is a continuous task and therefore also very time-consuming.
- Whitelists suggest completeness, but this cannot be given, as there can/will always be new providers and solutions that might be even more suitable, but have not yet been listed.
- They are bureaucratic, not flexible and do not allow any deviation. This often leads to the use of unauthorised tools in organisations, as employees want to use “their” best solution and not one that has been classified as suitable by a central office in the company.
It is also often argued that the criteria that must be met for inclusion on a whitelist are unclear. This problem exists in companies, but it is not so much a problem of a positive list as a whitelisting problem in itself, which reveals possibilities for improvement in handling and communication.
With application whitelisting there is also a problem with the numerous updates and upgrades of programs. A well maintained list not only names a product X from manufacturer Y, but also defines the exact version number, because this is the only way to ensure the best possible security. In other words: Version 7.2.3 of product X from manufacturer Y is listed, but newer versions are not. This often leads to older product versions being used, especially in larger corporations, because the testing and thus the release of a new version is very complex.
Impulse to discuss
When does it make sense for companies to use both a whitelist and a blacklist?
Notes:
[1] Of course, organisations are free to understand whitelists as recommendations without binding character; in such a case, the consequences mentioned above are not applicable.
[2] For the benefit of non-discriminatory language, it may be useful to replace the terms whitelist and blacklist with positive list or allowlist and blocklist.
Pursuant to Section 9 (8) GlüStV 2021, the Joint Gaming Authority of the Länder shall publish a joint official list on the internet listing the organisers and brokers of games of chance who hold a permit or licence pursuant to the GlüStV 2021.
The exact origin of the term whitelist is unclear. One of the earliest documented uses in the context of computer security dates back to the early 1990s. In a paper entitled “Firewall Design: Consistency, Completeness, and Compactness” published in 1992, researchers Steve Bellovin and Bill Cheswick used the term to refer to a list of trusted hosts or networks that were allowed to access a particular network or service.
If you like the article or would like to discuss it, please feel free to share it in your network. And if you have any comments, please do not hesitate to send us a message.
Here you can find additional information from out Smartpedia section: