Software security as part of UX
We all long for security and watch as it disappears. A plea for new perspectives on software security as part of the user experience.
Spring 2025: Family gathering in the garden. Three generations are gathered around the barbecue. The phone rings. Peter (29) answers. He works as a sales representative for a software company. A friendly female voice greets him and touts a new fibre optic connection. ‘A sales call!’ he recognises immediately. He wants to end the conversation politely and quickly. But something seems strange to him. Suspicious, he asks, ‘Am I speaking to AI?’ The person on the other end replies promptly, ‘Yes, I am artificial intelligence. Are you interested in a low-cost fibre optic contract?’ Peter hangs up. That day, he agrees on a ‘safe word’ with his family, a word that only they know. Better safe than sorry.
The paradox of security
The term ‘security’ generally refers to a state of being protected from danger and harm. We generally think security is great. But only if we don’t have to do anything extra or restrict ourselves to achieve it. This is because security seems to contradict other things that we also value highly, such as freedom, progress and simplicity. At least, that’s what we think.
Let’s test this hypothesis: in a state of uncertainty, we would probably never feel freer or more progressive, nor would we think that everything has become easier. Consequently, ‘security’ is neither a contradiction nor an ultimate goal: we perceive ‘high security’ or ‘lack of security’, but never maximum security. There is always something we can do to improve our security. But before we get too philosophical, let’s turn to the question I want to explore in this article: What happens when we look at software products through ‘security glasses’? When we view security not as a burdensome legal requirement, but as part of the user experience that is oriented towards the user?
What is software security?
Software security primarily means designing the system environment from the ground up to be as secure as possible and protecting it from harmful external attacks. This involves ensuring the integrity, authentication and availability of software. In the field of business software, this often includes both technical (development) measures and user training. Various DIN standards regulate the requirements and quality characteristics of secure software, especially in highly sensitive areas such as medicine or banking. So far, so familiar and so important.
However, the topic of software security is less frequently considered from the user’s perspective.
- What does ‘secure’ software mean for our users?
- How do they perceive our security measures?
- What ‘dangers’ lurk within our software?
- Does our software expose users to health risks, for example in the form of dependency, addiction, stress or back pain?
- Where do we as a company deliberately accept that users may be harmed in order to increase our profits?
This broader concept of security becomes particularly clear when we look at current technological developments. Every new technology brings not only new opportunities, but also new risks that go far beyond traditional IT threats and confront us with completely new questions about what it means to make software truly secure.
New technologies, new dangers
As the introductory story shows, rapid technological development brings with it entirely new challenges. The market for artificial intelligence is currently still largely a ‘Wild West,’ with important laws and clear regulations lacking in many areas. Nevertheless, new AI helpers are appearing in more and more software products – often unasked for – to support us in our everyday lives.
But AI is not just a silent tool like a calculator; it is a system that communicates with us in an almost human way and is thus able to influence our thinking and decisions. This new type of interaction harbours enormous potential, but also considerable risks if we do not handle it responsibly.
We are already seeing so-called ‘dark patterns’ becoming increasingly acceptable. These are design elements that deliberately steer users in a certain direction, for example, by tempting them to disclose personal data or conclude contracts that they do not actually want. Such manipulative designs have always existed, but the possibilities for using them inconspicuously and effectively are increasing – and with them, tacit acceptance.
The result: security becomes a bargaining chip. Instead of protecting users, their attention becomes a commodity. This is precisely why it is more important than ever to take a critical look at how new technologies are being used and how we as developers can take responsibility for ensuring that security does not fall by the wayside.
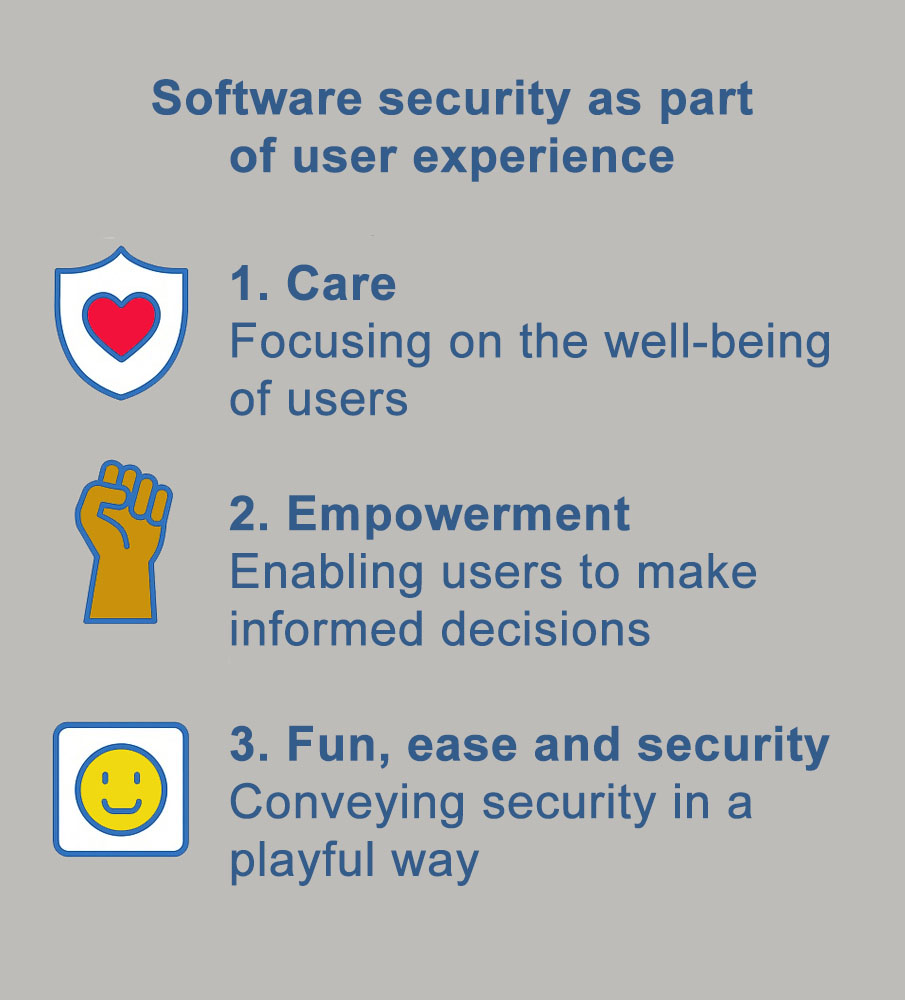
Three approaches to software security as part of the user experience
It is precisely in areas where there is still little regulation that we have the opportunity to play a positive role as pioneers. This is a real unique selling point (USP). To do this, we need to be aware of the following in software development: Many users trust our products blindly. As experts and professionals, we should therefore take responsibility. Here are three possible approaches:
1. Care
Care means doing things for someone’s benefit that they cannot do for themselves. The majority of users probably do not know where and how their data is stored. They do not check every day for security updates and do not spend hours dealing with complex rights management and data protection settings. We should take care of things they cannot do themselves. To do this, however, we first need to find out who is using our software and where these people need help. Note: Care does not mean patronising people.
2. Empowerment
Users can become aware of the options available to them and decide for themselves what they need to achieve their goals. In concrete terms, this could mean for software: You can decide whether you want to unlock a certain feature (you are aware of the possible security risks) or whether you want to provide additional data to make processes easier. We don’t force you and take a clear stance against dark patterns.
3. Fun, ease and security
Software security often has a ‘heavy’, unattractive character. Images of thick safes, massive padlocks and red danger signs flash before our inner eye. These are symbols that have shaped our user interfaces for decades. Can security also look ‘lighter’? Can it be more playful? Do I have to yell at users when they assign passwords: ‘Your password is weak, you weakling!’ or can I guide them to a secure password in a playful way? Examples such as ‘The Password Game’ [2] or ‘Gandalf Game’ [3] provide inspiration. Caution: playing can be addictive!
Speaking of playing, login processes today sometimes seem like reverse escape room games. From the user’s point of view, the 8-factor authentication before a video meeting that has already been running for five minutes is not very pleasant. How could this be made easier without neglecting security aspects? This is an exciting design challenge at the interface between user experience, security and technical feasibility.
Conclusion
We all long for security. But security is not a given; it must be constantly rethought, redesigned and filled with life. To achieve this, we need more diversity of perspectives, education and a creative, courageous approach to the topic of software security.
Security should play a much greater role in the user experience and not be a heavy, daunting topic. It is not about making everything more complicated, but about consciously ensuring that simplification does not become an invitation to manipulation.
Our users trust our products. This trust is our most valuable asset and we have a responsibility to protect and strengthen it.
Software security is not a technical detail, but a promise. One that we must keep.
Notes:
Looking for organic intelligence for future-proof software projects? Find out more about Anna Zinsser on her website. Or follow her on LinkedIn for playful insights into user experience, collaborative teamwork and experience-based learning.
[1] A true story, but the name and subject have been changed
[2] Neal Agarwal: The Password Game
[3] Lakera: Gandalf Game
If you like this article or would like to discuss it, please share it with your network. And if you have any comments, please do not hesitate to send us a message.
Anna Zinsser has published more articles on the t2informatik Blog, including

Anna Zinsser
Anna Zinsser is a UX designer, game developer and systemic transformation facilitator. As a freelancer, she has been supporting the development of digital solutions with a focus on user needs since 2017. As co-founder of denkhafen, she supports individuals, teams and organisations in times of change, personal development and self-organisation – creatively, systemically and with playful ease. To this end, she develops her own (analogue) games and workshop formats that enable experience-based learning in companies.
In the t2informatik Blog, we publish articles for people in organisations. For these people, we develop and modernise software. Pragmatic. ✔️ Personal. ✔️ Professional. ✔️ Click here to find out more.